-
A complex, lifecycle approach to addressing Advanced Persistent Threats
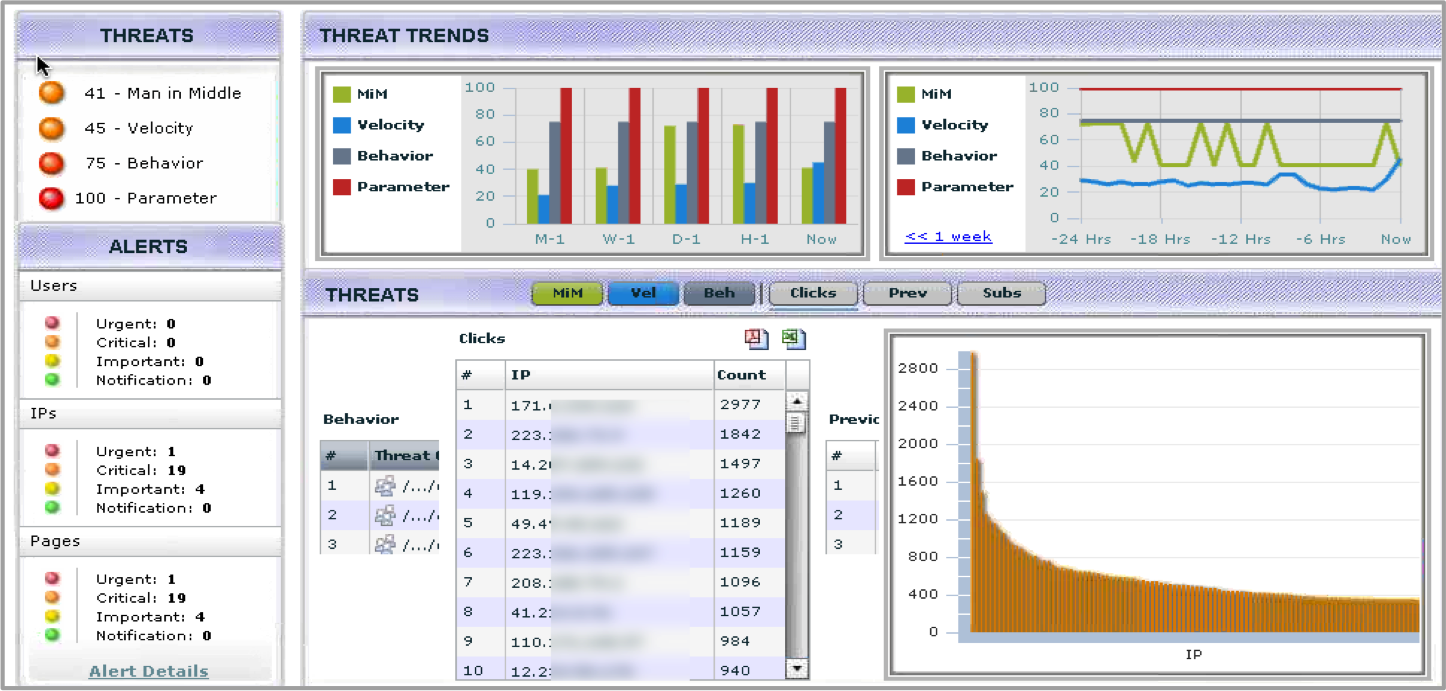
Today’s threat landscape is populated by increasingly sophisticated intrusions that take the form of advanced persistent threats, advanced targeted attacks, advanced malware, and zero-day threats. With all of the data breaches making the news, addressing sophisticated threats is top of mind for most executives. Enterprises are experiencing material security breaches as a result of these attacks, because advanced security operations teams operate in silos with no ability to share information across the entire security organization or environment. While Sandbox approach are everywhere these days, this is only one part of a coordinated security effort to combat increasingly sophisticated attacks.
Besides our solutions that collects and analyzes massive amounts of real-time data for all traffic to provide complex intelligence and real-time analysis of user behavior and our enterprise governance, risk, and compliance (GRC) which allows you to manage the lifecycle of corporate policies, assess and respond to risks and also to model you incident response procedures, we also provide endpoint security solutions for an end-to-end security approach.
